Two new social engineering attacks to look out for: ClickFix and Fake Captcha Phishing
The UC Davis Health Cybersecurity team has received notice of two new social engineering attacks called ClickFix and Fake Captcha. Both of these phishing attempts are similar in that they require users to willingly download malware on their computer using PowerShell; however, the actions that get the user to download it are different.
What is ClickFix phishing?
ClickFix is a phishing technique that attempts to lure users to copy and run PowerShell to download malware. PowerShell is a computer task automation that runs on every user’s computer. It is designed to automate the management of systems and build, test, and deploy solutions. As the name suggests, ClickFix phishing attempts offer the user a way to “click and fix” a fake problem by having them copy and paste a malicious command into PowerShell and run it.
What is Fake Captcha phishing?
Fake Captcha phishing is a technique similar to ClickFix in that it has users copy and paste malicious commands into PowerShell; however, how users obtain the malicious command is different. This social engineering technique uses the “Verify You are Human” dialogue box with the “I Am Not a Robot” verification. Instead of having the user “select all the buses” via pictures, it will ask them to press keys on their computer to verify their identity.
Examples of ClickFix phishing attempts:
Here are some of the ways ClickFix “fake problems” have been presented.
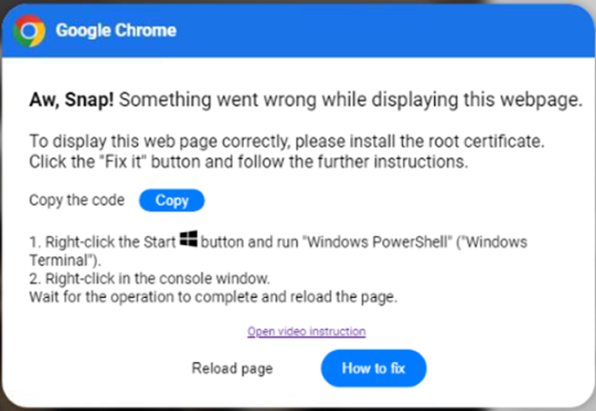
- A browser popup asks the users to open a malicious URL (click on Fix It). The user is directed to copy the code, open PowerShell, and run the malicious code, thus infecting their computer. This attempt looks very realistic and even includes a link to a video on how to “fix” the issue.
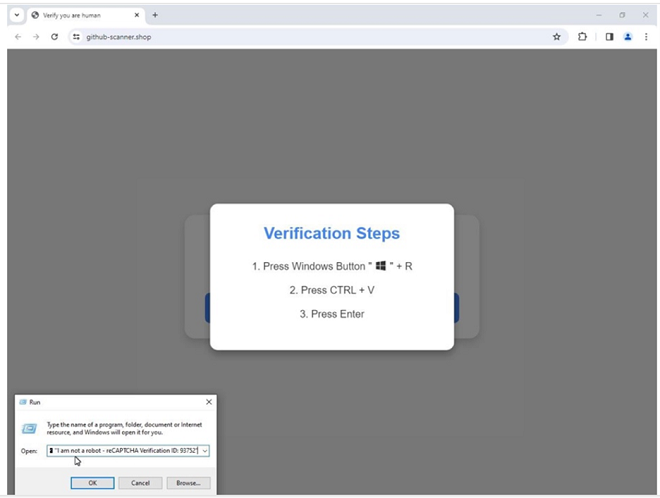
- Using GitHub notifications (for activity) to deliver malware. The perpetrator either commented on or created an issue in a GitHub repository, thus creating the notifications if the repository owner, issue owner, or other relevant collaborators have email notifications enabled. The notification is impersonating as a security warning from GitHub and includes a link to a fake GitHub website. From there, the fake website will use the Fake Captcha and ClickFix social engineering techniques to trick the user into executing a PowerShell command on their computer.

- Fake software updates used to deliver malware. Emails that masqueraded as “security updates” used “benign” email messages to instruct users to copy and paste malicious code into PowerShell on their computers. The emails typically do not contain any malicious links or attachments and are simply instructions.
Examples of Fake Captcha phishing attempts:

Real Captchas don’t ask users to press keys on their computer to verify their identity.
Both of these social engineering attacks prey on people’s innate desire to be helpful and independent by providing a simple way to “fix” an issue and move forward. It empowers users to complete the task without alerting their IT team and bypasses security protections by having the person infect themselves.
How to protect yourself and UC Davis Health
The UC Davis Health Cybersecurity team encourages staff to remain vigilant in their efforts to avoid phishing attacks. The best practice against ClickFix and Fake Captcha attacks is to always contact the Help Desk whenever you have an issue that needs to be fixed. You can reach the Help Desk at 916-734- HELP (4357).
For more information about phishing attacks, check out the articles listed below.




