Malicious advertising targets UCPath – beware of this new phishing attack
A new form of phishing has targeted the UC system’s UCPath. This malicious advertising, called malvertising, is a relatively new cyberattack technique that can use digital ads to fool users into revealing their username and password or clicking to install malware. Difficult to detect by both internet users and publishers, these malicious ads are usually served to consumers through legitimate advertising networks such as ads on Microsoft Edge, Google Chrome, or Safari.
Whenever you type a query into an internet search bar, you may often notice that your top few hits are labeled as “sponsored.” These are advertisements that companies pay for to push their results to the top of a search query. However, cybercriminals are now infiltrating these sponsored advertisements to impersonate real companies.
Their latest target: University of California, UCPath.
How does this attack work?
Malvertising combines several cybersecurity threats to complete an attack. Recently, criminals advertised a fake University of California UCPath website to fool UC employees into divulging their credentials.
Once the infected “sponsored ad” was clicked on, the screen that appeared looked exactly like the standard login page, prompting for a username and password. Once the user enters their credentials, the system captures them. They were then directed to a non-working page. Afterward, the criminals log into the victim’s UCPath account using the supplied credentials and update the victim’s direct deposit information to a new destination. In many cases, by the time the user realizes something has changed, it is too late.
In the image below, notice the “sponsored” links in the search results from Google. Can you tell which of these links leads to a malicious site? This is a great example of website spoofing.
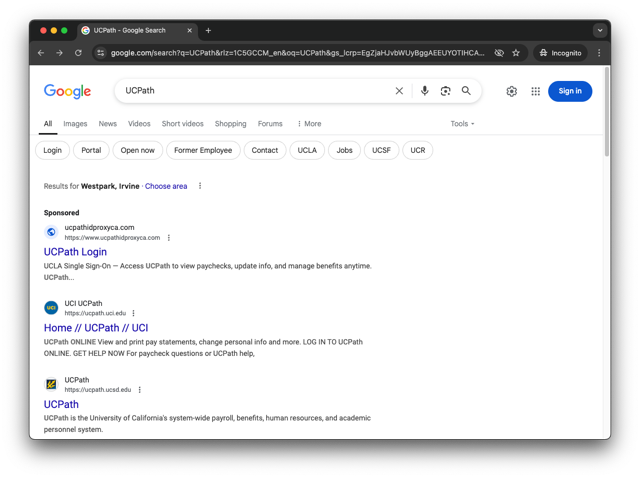
What is spoofing?
Spoofing is a technique through which a cybercriminal disguises themselves as a known or trusted source. Spoofing can take many forms, such as emails, GPS, calls, and more.
Other forms of malvertising attacks
Malicious software can be installed on your system when you click on harmful links or ads. These programs can steal your information, damage files, take over your computer, or demand ransom payments. Sometimes, you don’t even have to click—just viewing an infected ad (called a "drive-by download") or having your browser automatically redirected to a malicious site can lead to an attack.
What to look for
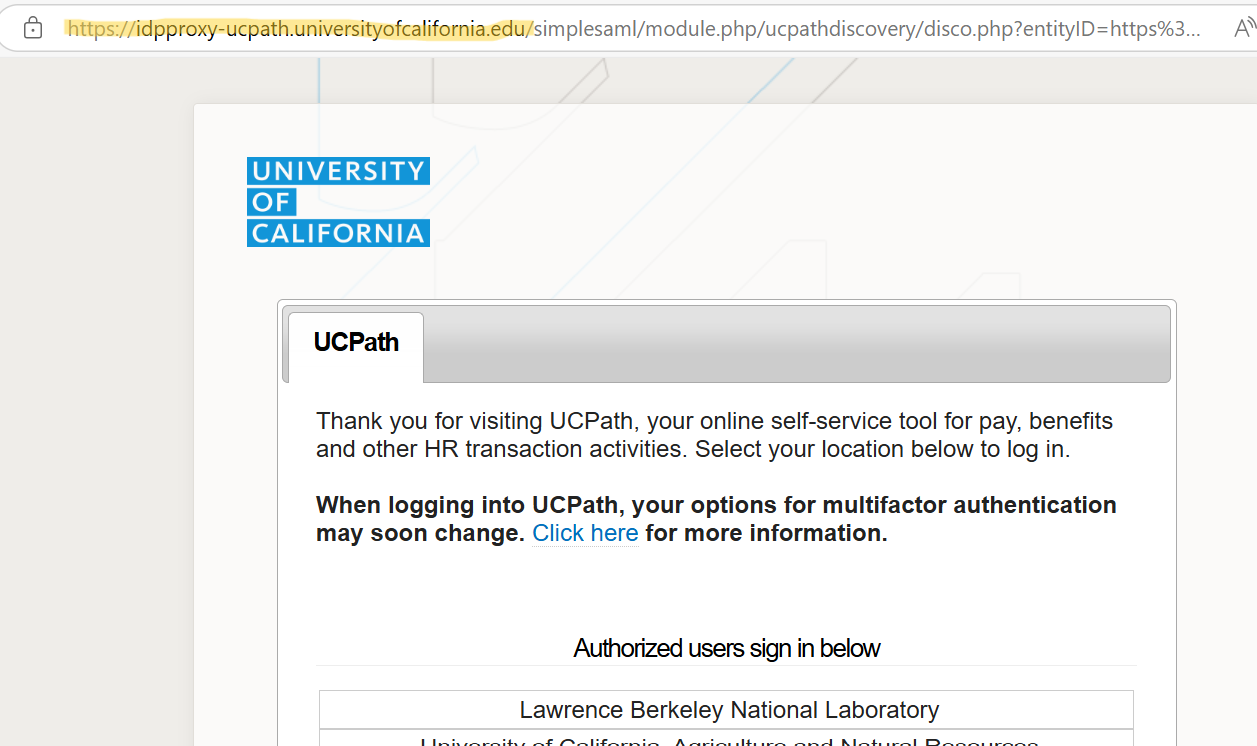
Beware of browser search results! Be on the lookout for URLs that are “close” to the correct one but aren’t or might be plausible, but are still not correct. Some examples include:
FAKE: ucpathsd.org/work/
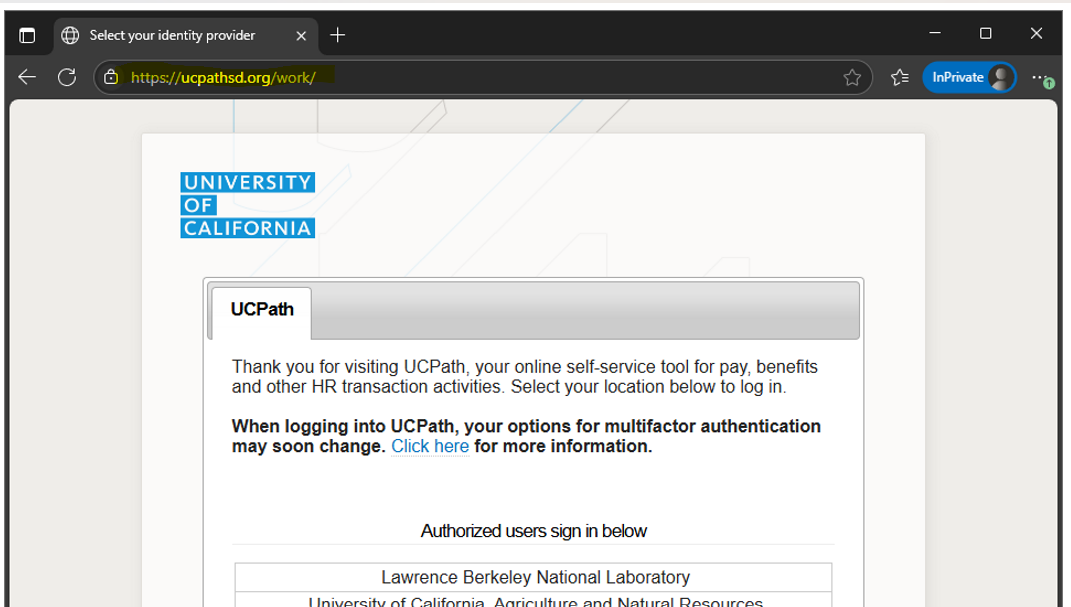
REAL: idpproxy-ucpath.univerityofcalifornia.edu
What to do
When using a browser search function, it is recommended to avoid using the “sponsored” search results at the top of the results. Scroll down to find the unsponsored URL. If you select one of these, be sure that the URL is known to you and matches exactly what you expect.
To verify a URL’s correctness, you should:
- Go to a known source for that URL, such as the UC Davis Health Intranet, and use that URL to reach the desired webpage
- Save appropriate URLs in your web browser “favorites” for critical websites you visit often or that house sensitive data (such as UCPath) to avoid searching
Although it's impossible to completely prevent phishing attacks, the best defense is awareness. Understanding the different types of phishing and how to identify them is key. Explore the articles below to learn more about common phishing tactics and how to protect yourself.
Resources:




